Linux Security Basics
Linux User& Groups
- User file: /etc/passwd
shell
[09/04/25]seed@VM:~$ head -5 /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/syncexplain:
cpp
sync : x : 4 : 65534 : sync : /bin : /bin/sync
name pswd UID GID home dir shell- the REAL password file: /etc/shadow
shell
[09/04/25]seed@VM:~$ sudo cat /etc/shadow | grep seed
seed:$6$n8DimvsbIgU0OxbD$YZ0h1EAS4bGKeUIMQvRhhYFvkrmMQZdr/hB.Ofe3KFZQTgFTcRgoIoKZdO0rhDRxxaITL4b/scpdbTfk/nwFd0:18590:0:99999:7:::
// actual password is: deesAccess Control
An introduction to Linux Access Control Lists (ACLs)
- ccess ontrol ist
三种用户类型:User, Group, Other
三种访问权限:Read, Write, eXecute
shell
[09/04/25]seed@VM:~$ ls -la | grep Music
drwxr-xr-x 2 seed seed 4096 Nov 24 2020 MusicKEEP IN MIND:
default permission level:
shell
[09/04/25]seed@VM:~/Documents$ umask
0002
[09/04/25]seed@VM:~/Documents$ touch eg1 && ls -ld eg1
-rw-rw-r-- 1 seed seed 0 Sep 4 02:41 eg1
[09/04/25]seed@VM:~/Documents$ umask 0077
[09/04/25]seed@VM:~/Documents$ touch eg2 && ls -ld eg2
-rw------- 1 seed seed 0 Sep 4 02:42 eg2explain:
original: 110 110 110
umask: 000 000 010 (0002)
(umask为1的话 原值归零)
new val: 110 110 100
-rw- rw- r-- [1 seed seed 0 Sep 4 02:41 eg1]
original: 110 110 110
umask: 000 111 111 (0077)
(umask为1的话 原值归零)
new val: 110 000 000
-rw- --- --- [1 seed seed 0 Sep 4 02:42 eg2]- ull ccess ontrol ist:
shell
[09/04/25]seed@VM:~/Documents$ getfacl eg1
# file: eg1
# owner: seed
# group: seed
user::rw-
group::rw-
other::r--
[09/04/25]seed@VM:~/Documents$ setfacl -m seed:rwx eg1
[09/04/25]seed@VM:~/Documents$ sudo chown root eg1
[09/04/25]seed@VM:~/Documents$ getfacl eg1
# file: eg1
# owner: root
# group: seed
user::rw-
user:seed:rwx
group::rw-
mask::rwx
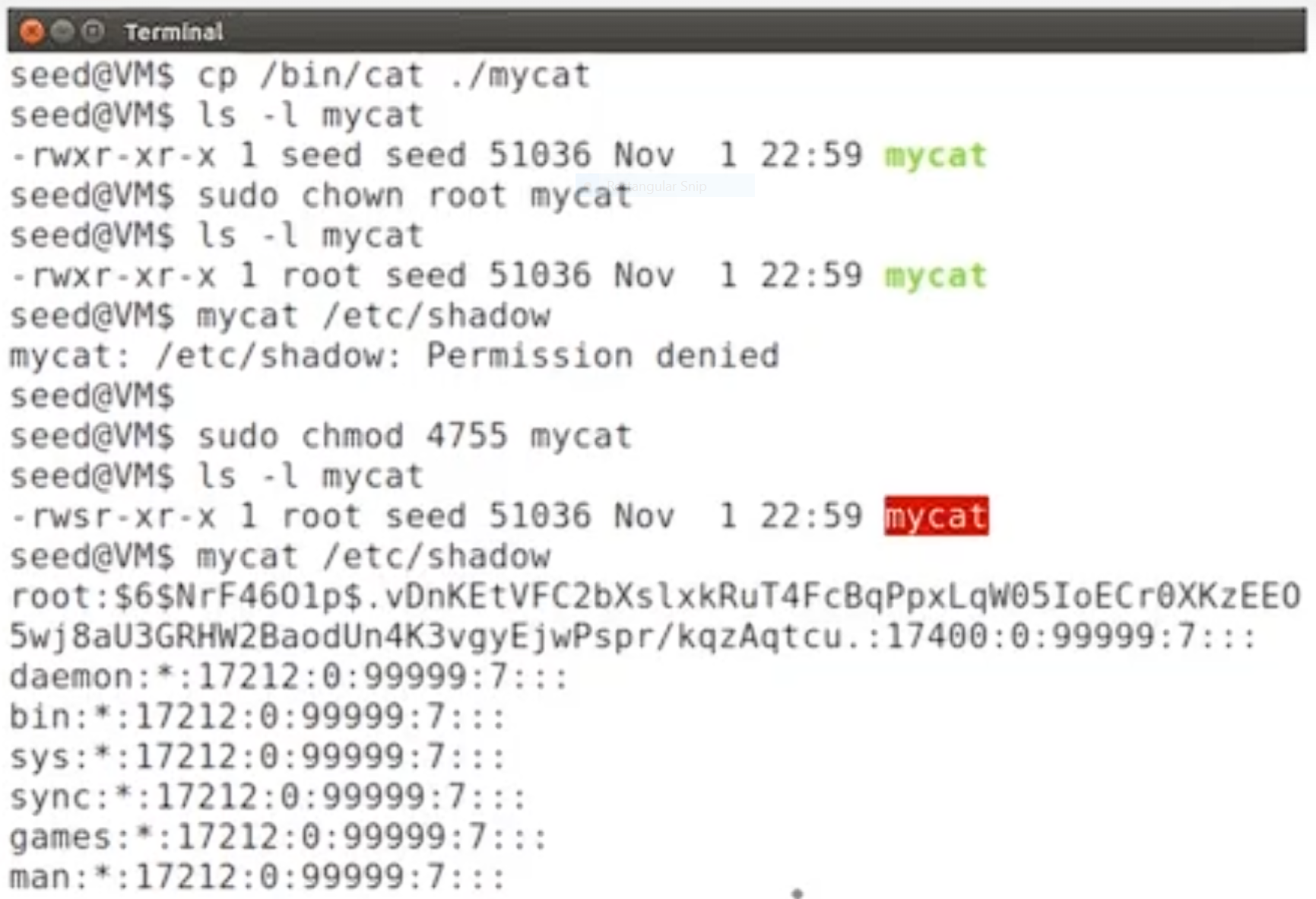
other::r--Set-UID technics
Set-UID programs:
- real UID: whoever execute the program
- effective UID: the OWNER of the program
when process try to access the file, it's the effective UID which is to be checked!
Turn a program into Set-UID program
| owner | group | other
_X_ _Y_ _Z_ _r_ _w_ _x_ _r_ _-_ _x_ _r_ _-_ _-_
X: Set-UID ———— when toggled, set owner UID to effective UID
y: Set-GID ———— vice versa(?)shell
# crack gf's pc in 10 secs!
# under gf:
$ cp /bin/sh /tmp/goofysh
$ chmod 4754 /tmp/goofysh
# under mine:
$ /tmp/goofysh
[GET!]What can go wrong?
Attack Surface
攻击表面,是指软件环境中可以被未授权用户(攻击者)输入或提取数据而受到攻击的点位(攻击介质)。
Attack via Env Variables
ざこざこご主人~  Cover Girl 115
Cover Girl 115
Computer Securityhttps://coderama.top/posts/2025/250904
赞赏博主